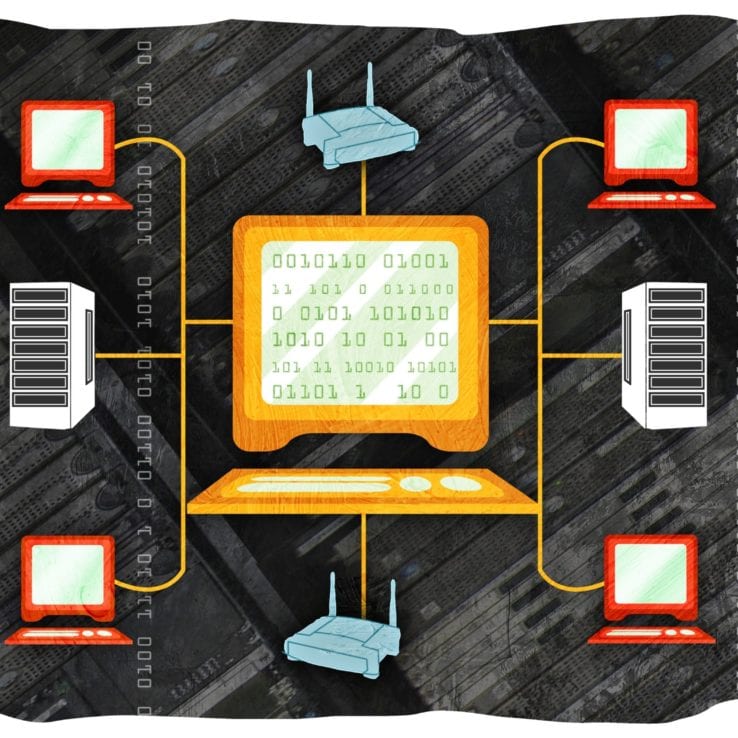
Protect Client Data at All Costs!
For business owners, client data is one of the most valuable assets you manage. Every email address, contract, payment detail, or personal record entrusted to your company represents trust. When that trust is compromised, the consequences can be immediate and long-lasting. Protecting client data is no longer just an IT issue. It’s a core business…